Repeat the Problem 1 using the directed Laplacian-based approach.
1. For the graph G shown in Figure 10.1, compute the following using the weight matrix–based approach:
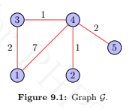
(a)
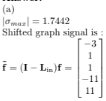
(b)


(c)
You might also like to view...
What does the ping -t ip address command do? (Select all that apply.)
a. It pings the host at the specified IP address until it is stopped. b. It pings the MAC address of the host at the specified IP address. c. It allows the ping to pass through routers. d. It allows the ping command to be executed from the command prompt.
Is it possible for an interactive system to be efficient without being effective? Why or why not?
What will be an ideal response?
RF signals can be picked up from an open or mis-configured AP.
Answer the following statement true (T) or false (F)
Confidentiality controls include data classification, data encryption, and proper equipment disposal.
a. true b. false