If an attacker decides to implement a less obvious port-scan, or stealth attack, which of the following techniques would be appropriate to make their activities more difficult to detect?
A. increase their scan speeds
B. limit their tool set
C. increase their scan speeds
D. limit their scan speeds
Answer: D
Computer Science & Information Technology
You might also like to view...
______ parameters were defined in Algol and are generally not used any more.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The command to scroll the current window to the right / left is:
a: [Alt->] / [Alt-< ] b: [Ctrl-r] / [Ctrl-l] c: [Ctrl-x] r / [Ctrl-x] l d: [Alt-r] / [Alt-l] e: [Ctrl->] [Ctrl-<]
Computer Science & Information Technology
Data exits a queue in the same order in which it entered the queue.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
?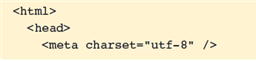
A. a child of the html element B. the parent of the meta element C. Both A and B. D. Neither A nor B.
Computer Science & Information Technology