All of the following would be examples of ways to increase security on a network EXCEPT ________
A) installing bio metric equipment
B) disabling e-mail
C) setting up usernames and passwords
D) giving only a few users permission to view sensitive files
B
Computer Science & Information Technology
You might also like to view...
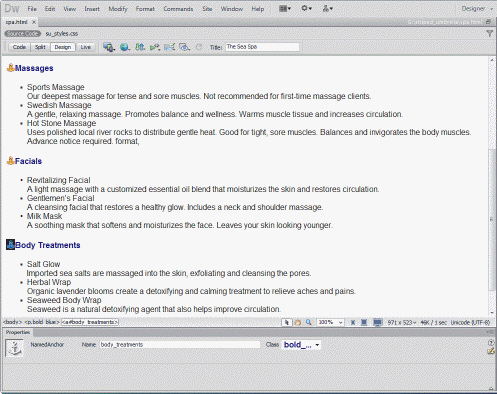 Named anchors, as shown in the accompanying figure, should contain only ____.
Named anchors, as shown in the accompanying figure, should contain only ____.
A. uppercase characters B. alphanumeric characters C. lowercase characters D. special characters
Computer Science & Information Technology
What is the protocol developed by Cisco for enterprise-wide routing environments?
A. RIP B. OSPF C. BGP D. EIGRP
Computer Science & Information Technology
User agents render HTML documents from bottom to top.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
When you choose one of the options to send a worksheet via e-mail, a message opens in Microsoft Outlook with your workbook attached.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology