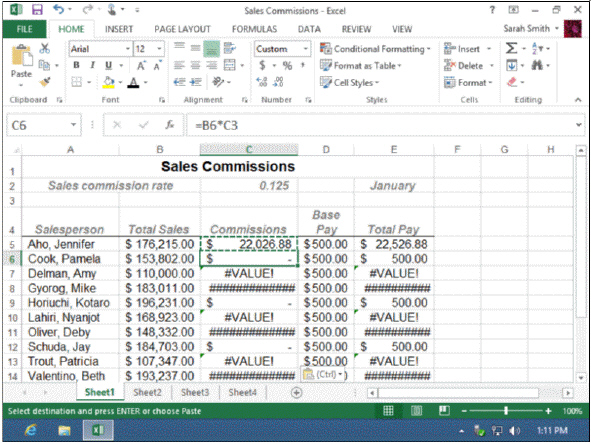
 In the accompanying figure, the original formula =B5*C2 works correctly in cell C5. When it is copied and pasted into cell C8, why do the hash marks appear?
In the accompanying figure, the original formula =B5*C2 works correctly in cell C5. When it is copied and pasted into cell C8, why do the hash marks appear?
A. The copied formula does not refer to the correct cells and produces a result that is too large to fit in the cell.
B. The copied formula contains a cell which is blank.
C. The copied formula contains a cell with a label.
D. none of the above
Answer: A
You might also like to view...
A(n) ______________________ is usually implemented as an array of linked lists, showing connections between vertices in a graph.
A. adjacency matrix B. connection matrix C. adjacency list D. connection array
The ________ is designed to make it easy to access the commands that you use most often in Excel
Fill in the blank(s) with the appropriate word(s).
Which type of firewall filter can match incoming traffic to the corresponding outbound IP address connection by way of IP address and port?
A. Packet filtering B. NAT filtering C. Application-level gateway D. Circuit-level gateway
A(n) ____________________ is a coding mistake made by a programmer during the development of a software program.
Fill in the blank(s) with the appropriate word(s).