____ is defined as a business process to service a request associated with an identity.
A. Workflow
B. DN
C. Provisioning
D. Data broker
Answer: C
Computer Science & Information Technology
You might also like to view...
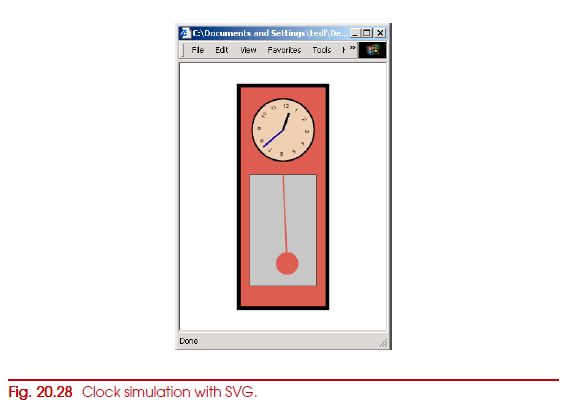
Create an SVG document that simulates a clock with a pendulum (i.e., hour hand, minute hand, pendulum). An example image is shown in Fig. 20.28.
Computer Science & Information Technology
Which type of macro can only be used with table events?
A) Data macros B) Stand-alone macros C) Embedded macros D) Event-driven macros
Computer Science & Information Technology
The Knowledge Consistency Checker (KCC) ensures the maximum number of hops between any two domain controllers does not exceed what number?
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
What filtering mechanisms do almost all main border firewalls use?
A. Static packet filtering B. NAT filtering C. Stateful packet inspection D. Application proxy filtering
Computer Science & Information Technology