List some devices that can form the endpoints of the VPN.
What will be an ideal response?
A server running VPN protocols (e.g., IPSec)
A VPN appliance, which is a special hardware device devoted to setting up VPN communications
A firewall/VPN combination: Many high-end firewall programs support VPN setups as part of their built-in features.
A router-based VPN: Routers that support IPSec can be set up at the perimeter of the LANs to be connected. These are also sometimes called IPSec concentrators. IPSec concentrators use a complex set of security protocols to protect information, including Internet Key Exchange (IKE), which provides for the exchange of security keys between the machines in the VPN.
You might also like to view...
A good reason for overloading an operator is to enable it to
A) outperform its C language counterparts. B) be used with types defined by the programmer. C) operate on more operands than in its standard definition. D) operate on no operands. E) None of the above
In the accompanying image of a Microsoft Word 2016 document, which of the following boxes points to the Close button??
?
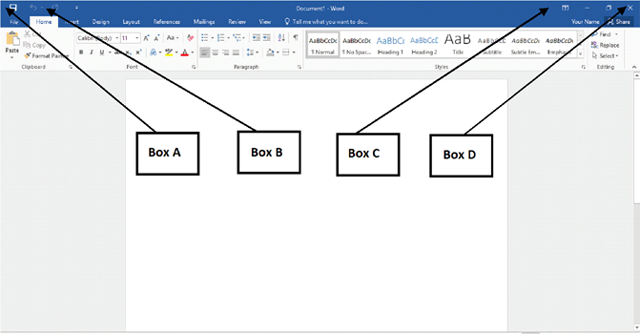
A. ?Box A B. ?Box B C. ?Box C D. ?Box D
In order to use a WBS in Project 2010, you must organize tasks into ____________________ tasks.
Fill in the blank(s) with the appropriate word(s).
____ is a way to allow Photoshop to create new frames automatically between two existing frames.
A. Filtering B. Editing C. Tweening D. Auto-filling