As a designer, you are constantly examining the fit between the ________, the ________, and the ________ set by the organization.
A) human; computer; tasks
B) human; display; tasks
C) designer; computer; tasks
D) human; display; feedback
A) human; computer; tasks
You might also like to view...
In the five steps of vulnerability management, prioritizing vulnerabilities should happen before mitigation of vulnerabilities
Indicate whether the statement is true or false
What is the decimal equivalent to the hexadecimal number D?
A. 13 B. 15 C. 12 D. 10
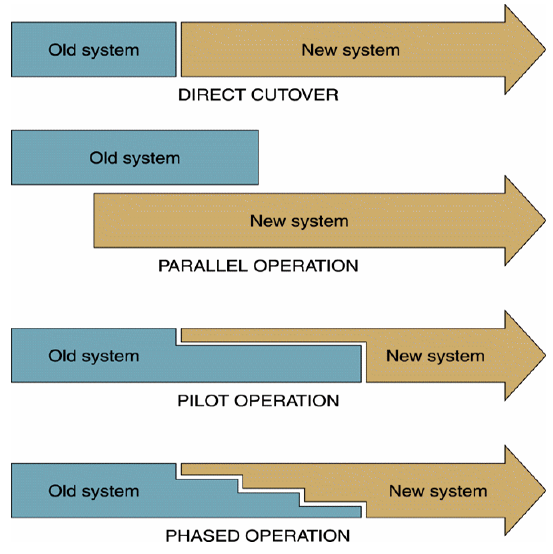
A. phased operation B. parallel operation C. pilot operation D. direct cutover
When tables are joined in a query, it is not possible to restrict retrieval by using criteria.
Answer the following statement true (T) or false (F)