Graph the point. 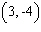
A. 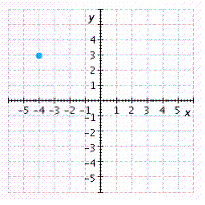
B. 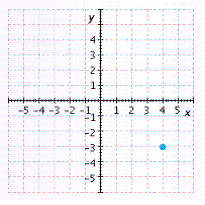
C. 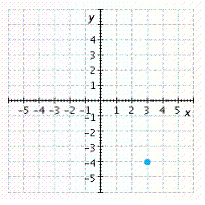
D. 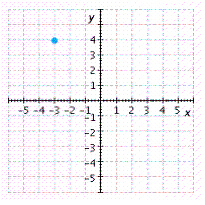
E. 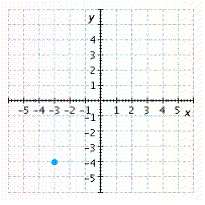
Answer: C
You might also like to view...
The role of the ____ part of the security process is to ensure that the selected approach represents the most effective security response, as well as the greatest cost benefit for the organization as a whole.
A. plan B. evaluate C. management D. design
The purpose of an interface is to:
a) provide similar objects with the same functionality, even though each will implement the functionality differently b) provide different objects with the same functionality, even though each will implement the functionality differently c) provide default implementations of methods and properties d) None of the above.
Which statement is false?
a. The Collections API provides a set of public static methods for converting collections to unmodifiable versions. b. Unmodifable wrappers throw ModificationExceptions if attempts are made to modify the collection. c. You can use an unmodifiable wrapper to create a collection that offers read-only access to others while allowing read-write access to yourself. d. You can create the kind of collection mentioned in part (c) simply by giving others a reference to the unmodifiable wrapper while you also retain a reference to the wrapped collection itself.
The Remove Background command always discards all the undesired picture components that make up the background.
Answer the following statement true (T) or false (F)