The accompanying figure shows the working of _____.
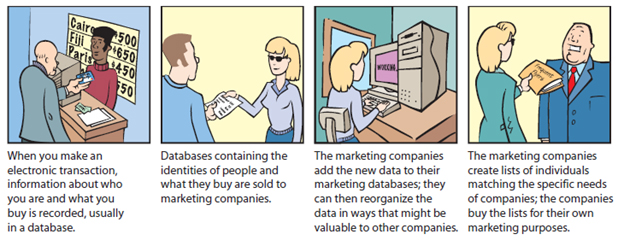
A. ?electronic profiling
B. ?big data
C. ?a surge suppressor
D. ?a data encryptor
Answer: A
You might also like to view...
As manufacturers develop new memory technologies, the speed and capacity of memory tend to ________, while the cost per storage unit tends to ________.
a) increase, increase b) increase, decrease c) decrease, increase d) decrease, decrease
In Excel, a number can contain the characters ____.
A. 0 1 2 3 4 5 6 7 8 9 B. + - ( ) , / C. . $ % E e D. all of the above
When you click the ________ button, the filter arrows are removed from the column titles but the color and shading formats applied from the table style remain
A) Convert to Range B) Available Windows C) Convert to Table D) Get External Data
List the error-control techniques for data integrity.
What will be an ideal response?