Consider the data set shown in Table 7.12.
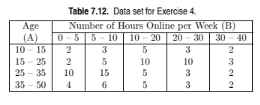
(a) For each combination of rules given below, specify the rule that has the
highest confidence.
i. 15
and 15
ii. 15
15
iii. 15
(b) Suppose we are interested in finding the average number of hours spent
online per week by Internet users between the age of 15 and 35. Write
the corresponding statistics-based association rule to characterize the
segment of users. To compute the average number of hours spent online,
approximate each interval by its midpoint value (e.g., use B = 7.5 to
represent the interval 5
Test whether the quantitative association rule given in part (b) is sta-
tistically significant by comparing its mean against the average number
of hours spent online by other users who do not belong to the age group.
(a)
I. Both 15
10
ii. The rule 15
(83.3%).
iii. The rule 10
(73.8%).
(b) There are 65 people whose average age is between 15 and 35.
The average number of hours spent online is
2.5×12/65 + 7.5×20/65 + 15×15/65 + 25×13/65 + 35×5/65 = 13.92.
Therefore the statistics-based association rule is:
15 ? A < 35 ?? B : ? = 13.82.
(c) 2.5 × 6/35 + 7.5 × 9/35 + 15 × 10/35 + 25 × 6/65 + 35 × 4/65 = 14.93.
The standard deviations for the two groups are 9.786 (15 ? Age < 35)
and 10.203 (Age < 15 or Age ? 35), respectively.
![]()
The difference is not significant at 95% confidence level.
You might also like to view...
List the three main software components that may fail when a client process invokes a method in a server object, giving an example of a failure in each case. To what extent are these failures independent of one another? Suggest how the components can be made to tolerate one another’s failures.
What will be an ideal response?
What operation does a binary search tree have for the elements in the tree that the linked list does not?
a. Finding the minimum and maximum elements b. Finding the average for all the elements c. There is no operation in a binary search tree that the linked list does not have d. Finding the pivot element to divide the tree.
Which of the following protocols was designed to address most of the consumer demands for privacy when using a credit card online?
A. TSL B. PGP C. SET D. S/MIME
Which of the following is not a format that is used for digital audio?
a. WMA b. WAV c. DOC d. MP3