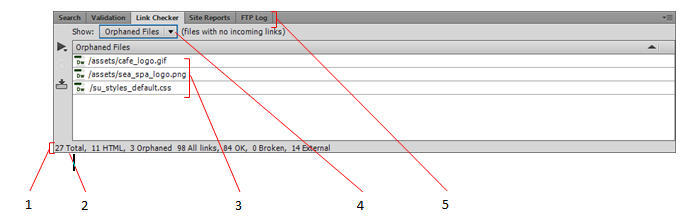
In the figure above, a total of ____________________ files were checked.
Fill in the blank(s) with the appropriate word(s).
twenty seven
Computer Science & Information Technology
You might also like to view...
All of the following are methods of the ArrayList class except:
(a) clear() (b) resize() (c) contains() (d) trimToSize()
Computer Science & Information Technology
________________ WEP solves the weak IV problem by rotating the keys frequently and uses different keys for different types of traffic.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
________ make(s) data easier to interpret by changing the data's appearance based on value
A) Conditional formatting B) Applying styles C) Side-by-side tables D) Sorting and filtering
Computer Science & Information Technology
Which of the following biometric methods scans the ridges of a finger for matching?
A. fingerprint scanning B. finger scan C. hand geometry scan D. hand topography scan
Computer Science & Information Technology