To help prevent loss of information, software vendors, including Microsoft, now provide whole disk encryption. This feature creates new challenges in examining and recovering data from drivers. What are four features offered by whole disk encryption tools that forensics examiners should be aware of?
What will be an ideal response?
The following are features offered by whole disk encryption tools that forensics examiners should be aware of:?-Preboot authentication, such as single sign-on password, fingerprint scan, or token (USB device)-Full or partial disk encryption with secure hibernation, such as activating a password-protected screen saver-Advanced encryption algorithms, such as Advanced Encryption Standards (AES)? and International Data Encryption Algorithm (IDEA)-Key management function that uses a challenge-and-response method to reset passwords or passphrases
You might also like to view...
What is a Q R Code?
What will be an ideal response?
The ______________________ method retrieves long values.
Fill in the blank(s) with the appropriate word(s).
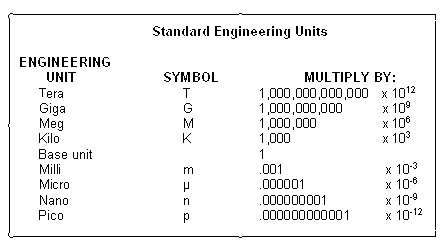 Item B in the accompanying figure is used to set columns of equal length.
Item B in the accompanying figure is used to set columns of equal length.
Answer the following statement true (T) or false (F)
An approach where the common disks are partitioned into volumes, and each volume is owned by a single computer is __________ .
A. server shared disks B. active secondary C. separate server D. shared nothing