_____ measures risk likelihood and impact.
A. Risk assessment
B. Risk marking
C. Risk identification
D. Risk control
Answer: A
You might also like to view...
PowerPoint allows you to change the thickness of a WordArt outline in ____ increments.
A. one-half-point B. one-fourth-point C. three-quarter-point D. one-point
Case Question 2Natalie is responsible for updating her company's Web site. Her boss has asked her to choose and apply three different table styles as possible changes to existing tables. She is instructed to take screenshots of each style and bring the images to the next company meeting along with her comments and an overall recommendation.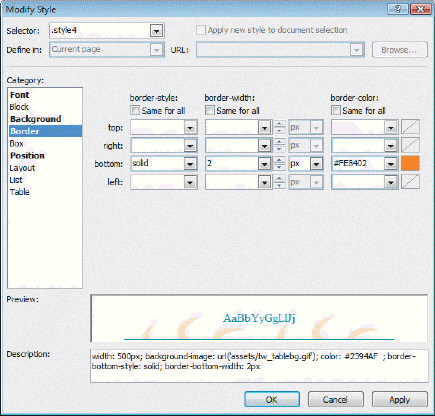 Referring to the figure above, Natalie has chosen what type of border?
Referring to the figure above, Natalie has chosen what type of border?
A. solid bottom border only for the selected cell B. solid bottom border only for the entire table C. style4 border for the entire table D. double solid bottom border only for the entire table
Which of the following is true of a client/server topology?
A. Virtual servers are used to stream data to other remote servers B. Servers are used to connect to centralized clients C. Remote clients connect to a centralized server D. Remote clients connect to each other via a virtual server
The secondary key
a. Is unique. b. May be used to access records. c. Is used within the record only. d. Is the same as the primary key.