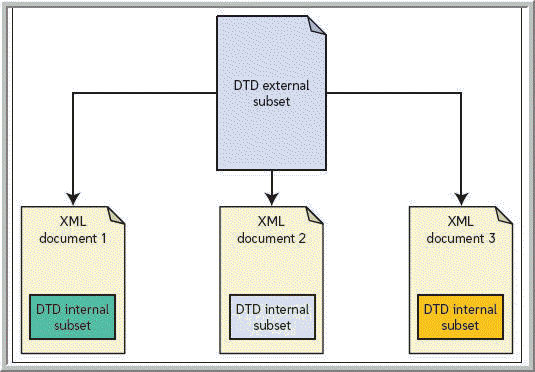
As shown in the accompanying figure, the external subset would define some basic rules for all of the documents, and the internal subset would define rules that are specific to each document.
Answer the following statement true (T) or false (F)
True
You might also like to view...
Method _________ returns a new string where all leading and trailing whitespace has been removed.
Fill in the blank(s) with the appropriate word(s).
A ________ allows a hacker to gain access to your computer and take almost complete control of it without your knowledge.
A. denial of service (DoS) B. zombie C. logic bomb D. rootkit
There are 20 laptops in a room and they all need to connect wirelessly to the network. Which of the following would be the BEST device to use?
A. Switch B. Router C. Access point D. Hub
After the RI1 . sued Napster,
a. the Supreme Court ruled in favor of Napster. b. Congress passed the Digital Millennium Copyright Act that legalized file sharing. c. Congress made peer-to-peer networks illegal. d. Napster renamed itself KaZaA. e. Napster went off-line.