Briefly describe the areas that should be considered when creating an incident response team (IRT).
What will be an ideal response?
IRTs are composed of individuals from the following areas:
* Senior management-These decision makers need to be involved and must understand the actual function of the IRT. They are the ones to give valuable business decisions in times of crisis.
* IT personnel-The chief security information officer and other IT management personnel can provide detailed assessment of the damage caused by the attack.
* Corporate counsel-The corporate lawyer should always be aware of the activities of the IRT. From beginning to end, the counsel should be present to ensure that no applicable laws are violated concerning the company or an individual.
* Human resources-If the IRT comes across incidents that involve employees, then an immediate response from Human Resources is needed. This includes checking to see whether certain incidents actually violate existing policies, and in extreme cases whether employees should be terminated or merely counseled.
* Public relations-Public image is often a major priority of an organization. Public Relations personnel should know the nature of the security incident because they often advise or decide on what can and cannot be said to the general public.
You might also like to view...
You can assign the contents of one array to another by using
A) the assignment operator. B) the equality operator. C) both array names. D) A and C together. E) none of the above.
You can use the Exists method to avoid the run time error that occurs when the computer cannot locate the file you want opened for input.
Answer the following statement true (T) or false (F)
Which group is this user a member of?
What will be an ideal response?
Reviewing User Account Properties
a. Click Start > Search for Control Panel > Select Administrative Tools > Select
Computer Management.
b. Select Local Users and Groups. Click the Users folder.
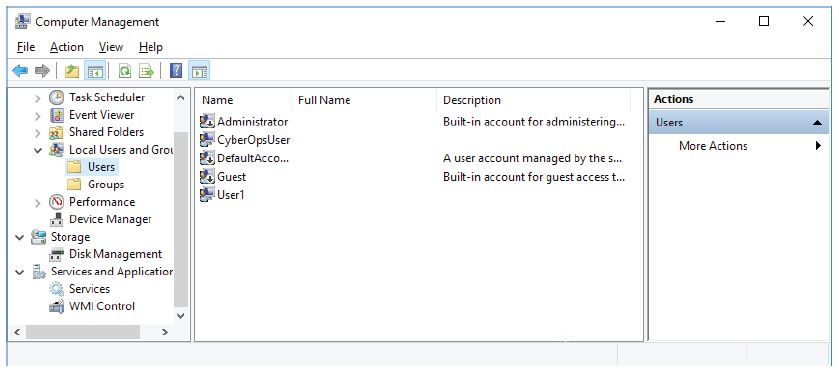
c. Right-click User1 and select Properties.
d. Click the Member Of tab.
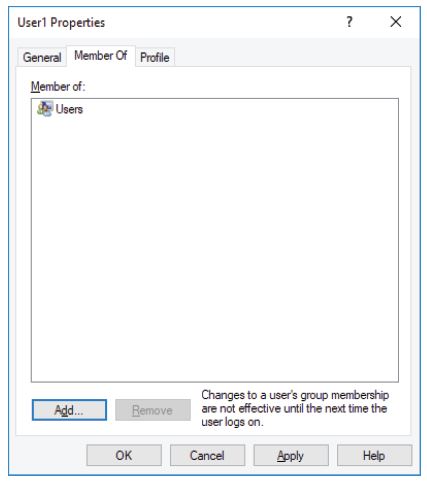
e. Right-click the account CyberOpsUser and select Properties.
Which command-line utility can be used to change an existing FAT or FAT32 partition to NTFS without losing data on the partition?
a. cipher b. convert c. encrypt d. fileconv