________ is the likelihood that a threat will exploit a vulnerability resulting in a loss
Fill in the blank(s) with correct word
Risk. Organizations use risk mitigation techniques to reduce risk.
Computer Science & Information Technology
You might also like to view...
Write the HTML code that produces the following Web page. The width of the table is 400 pixels and the border is one pixel wide. The header is enclosed in an H2 element.
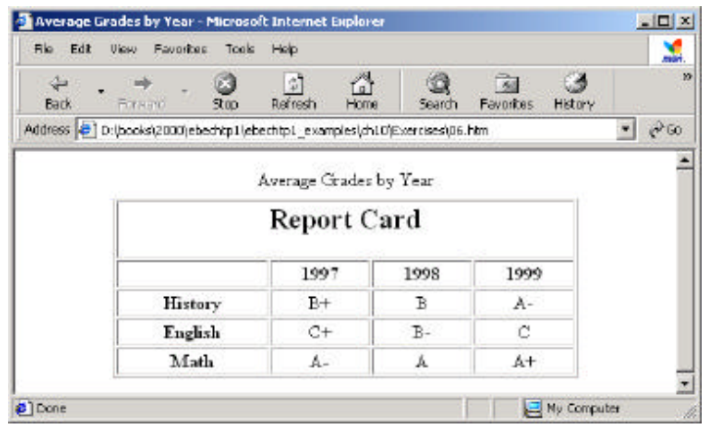
Computer Science & Information Technology
________ is the operator for performing multiplication
Fill in the blank(s) with correct word
Computer Science & Information Technology
If you have a worksheet with quarterly data that you want to show in a PowerPoiint presentation as well as a Word document and have editing changes reflected in both, you should use:
A) copying. B) grouping. C) linking. D) embedding.
Computer Science & Information Technology
CommView is an example of which of the following?
a. Key logger b. Packet sniffer c. Virus d. Tool for industrial espionage
Computer Science & Information Technology