The client can use a method without knowing how it is implemented. The details of the implementation are encapsulated in the method and hidden from the client who invokes the method. This is known as __________.
a. information hiding
b. encapsulation
c. method hiding
d. simplifying method
ab
You might also like to view...
For successful usability testing, a realistic ________ should be set up where the user is given a list of tasks to perform in the application
Fill in the blank(s) with correct word
Which of the following Mail Merge Commands from the Mailings tab opens the Mail Merge Recipients dialog box in order to sort records?
A) Rules B) Start Mail Merge C) Select Recipients D) Edit Recipient List
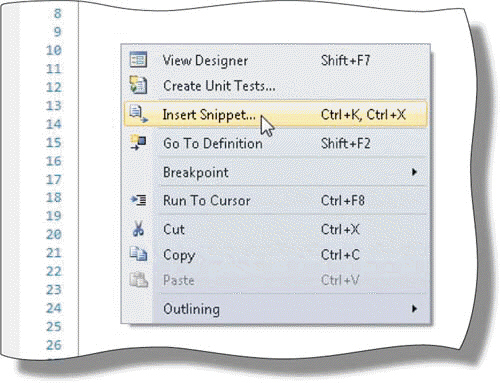 Visual Basic contains a code library of almost ____ pieces of code called code snippets, inserted by the command shown in the accompanying figure.
Visual Basic contains a code library of almost ____ pieces of code called code snippets, inserted by the command shown in the accompanying figure.
A. 125 B. 250 C. 500 D. 750
Customers may purchase prints or create greeting cards, mugs, and other gift items from their photos through any of Flickr's ____.
A. pages B. options C. affiliates D. services