Secure POP3 uses TCP port _______________.
Fill in the blank(s) with the appropriate word(s).
5
correct
You might also like to view...
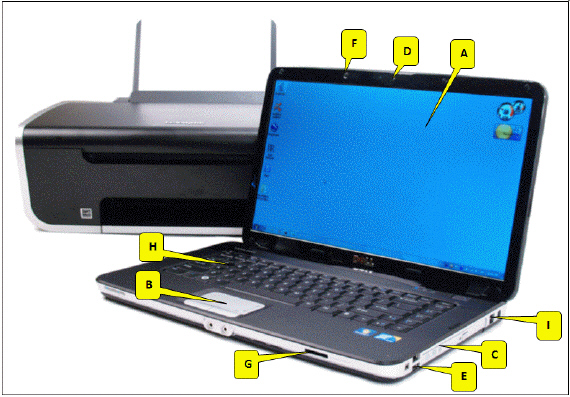 Referring to the accompanying figure, which of the following callouts points to the memory card slot?
Referring to the accompanying figure, which of the following callouts points to the memory card slot?
A. D B. G C. I D. C
You cannot override the order of precedence for arithmetic operators.
Answer the following statement true (T) or false (F)
Answer the following statements true (T) or false (F)
1. Under the Intel architecture, a task consists of a task state segment (TSS). 2. In the Intel architecture, the task execution space holds the code, stack, and data segments. 3. Memory protection helps to prevent one task from accidentally or intentionally changing the contents of memory assigned to another task. 4. In the Intel architecture, limit checking ensures that only code, data, or stack segment descriptors are used and that they are used as intended. 5. On a Pentium, privilege level 3 has the highest priority.
List the four factors critical to the success of an InfoSec performance program, according to NIST SP 800-55, Rev. 1.
What will be an ideal response?