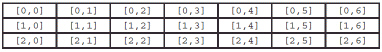
 The above table represents a one-dimensional array.
The above table represents a one-dimensional array.
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
Use the Repository feature to view the entry for the central process.
What will be an ideal response?
Computer Science & Information Technology
To use an image in a program, the image first must be ____ into the Resources folder.
A. linked B. attached C. imported D. synced
Computer Science & Information Technology
The internal vulnerability assessment is usually performed against every device that is exposed to the Internet, using every possible penetration testing approach. __________
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
What is Math.ceil(3.6)?
a. 3.0 b. 3 c. 4.0 d. 5.0
Computer Science & Information Technology