Defensive programming is sometimes referred to as _________.
A. variable programming
B. secure programming
C. interpretive programming
D. chroot programming
B. secure programming
Computer Science & Information Technology
You might also like to view...
For the following Web page, list all of the objects and actions
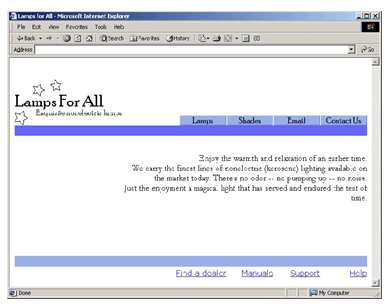
Computer Science & Information Technology
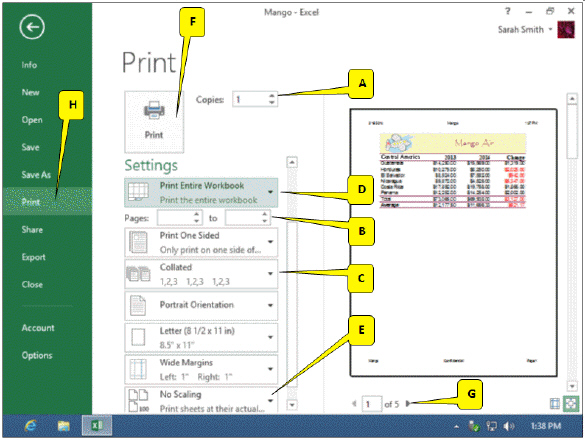 Referring to the accompanying figure, which callout points to the control that allows you to preview each page?
Referring to the accompanying figure, which callout points to the control that allows you to preview each page?
A. G B. D C. C D. E
Computer Science & Information Technology
Which of the following is the first packet sent in the TCP three-way handshake?
A. RST B. SYN C. ACK D. PSH
Computer Science & Information Technology
The ________ Wizard locates duplicate records in a table
Fill in the blank(s) with correct word
Computer Science & Information Technology