____ can ensure that the money that is invested in security provides the maximum benefit for the outlay.
A. Strategic evaluations
B. Focused evaluations
C. Stressed evaluations
D. Cost-based evaluations
Answer: B
You might also like to view...
Case-Based Critical Thinking QuestionsCase 18-1Sarah wants to learn more about computer programming and the techniques used to code a program. Since there are so many different programming languages, she has decided to start by working with Python. Sarah is learning the vocabulary of Python by examining what the language's keywords mean. When she sees PRINT, she knows it directs the computer to ____.
A. send the information to the printer driver B. display the text on the screen C. commit the instructions to memory D. carry out logical operations
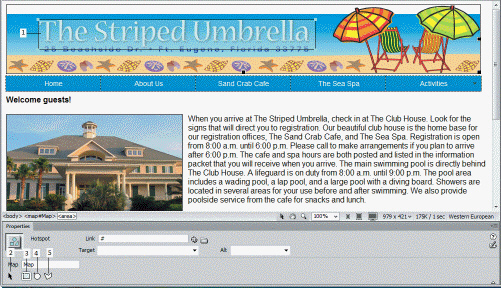 In the accompanying figure, Item ____ is the Pointer Hotspot tool.
In the accompanying figure, Item ____ is the Pointer Hotspot tool.
A. 2 B. 3 C. 4 D. 5
What provides reports and other useful data about your website?
a. Domain name b. Web host c. Name server d. Web analytics
Which of the following is NOT a method for entering data into a database?
A) capturing from a Web site B) importing from another source C) scanning a printed document D) using the keyboard