The three traversal algorithms we mentioned in the text for binary search trees are _______ , _________ and ____________.
Fill in the blank(s) with the appropriate word(s).
inorder, preorder, postorder
Computer Science & Information Technology
You might also like to view...
Show the hex addresses and variable values after the statements have been executed. (All pointers are 4 bytes!)
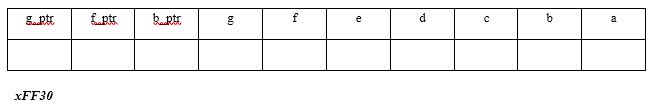
Computer Science & Information Technology
Which of the following refers to the abuse of electronic messaging systems to randomly or indiscriminately send unsolicited bulk messages?
a. phishing b. spamming c. phreaking d. shoulder surfing
Computer Science & Information Technology
When a(n) ____________________ no longer is needed, a user deletes it from a file.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The System.in class does not provide methods for reading numbers.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology