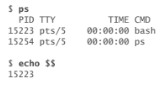
Name two ways you can identify the PID number of the login shell.
What will be an ideal response?
You might also like to view...
If your password is strong enough, do not change it.
Answer the following statement true (T) or false (F)
Shortly after ___________ signals stop arriving from a server, another server in the cluster takes over its functions.
Fill in the blank(s) with the appropriate word(s).
Match each task to the dialog box to accomplish that task:
I. XY chart II. single-series data series chart III. multiseries data series chart IV. default chart V. single- or multiseries chart A. column chart B. pie chart C. scatter chart D. clustered column chart E. doughnut chart
Employees are reporting that they are receiving unusual calls from the help desk for the purpose of verifying their user credentials. Which of the following attack types is occurring?
A. Vishing B. Spear phishing C. Phishing D. Pharming