Individuals who hack into systems at an organization's request but are not employed by the organization are known as blue hats
Indicate whether the statement is true or false
True —Blue hats are individuals asked by an organization to attempt to hack into a system who are not employed by the organization. Blue hats are often used when testing systems.
You might also like to view...
Each standard library has a corresponding:
a. Function. b. Variable type. c. Header. d. CD-ROM.
Planning a project by starting with broad categories of tasks is called the ____________________ method of creating a WBS.
Fill in the blank(s) with the appropriate word(s).
Case 2Andrew is preparing to publish a new Web site using a Web hosting company. He is researching connection types and reviewing the options available in Expression Web.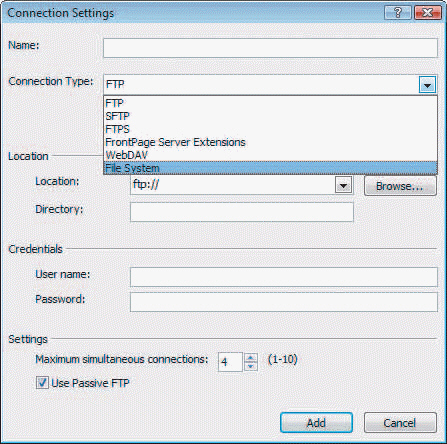 Referring to the figure above, if Andrew chooses to use FTP to transfer files from the source site to the publishing destination, what will he need to know?
Referring to the figure above, if Andrew chooses to use FTP to transfer files from the source site to the publishing destination, what will he need to know?
A. User name and password for his account. B. The address to publish to. C. The file path to the directory in which he plans to publish files. D. All of the above.
Which statement compares the string named gender to "Male"?
A. ?if(gender == "Male") B. ?if(gender.isequal("Male")) C. if(gender.equals("Male")) D. ?if(gender ="Male")