A good password will consist of:
A) symbols.
B) symbols, letters, and numbers.
C) letters.
D) numbers.
B
You might also like to view...
The following function should swap the values contained in two integer variables, num1 and num2. What, if anything, is wrong with this function?
``` void swap(int num1, int num2) { int temp = num2; num2 = num1; num1 = temp; } ``` a. You must first initalize temp to 0 before using it. b. The variable temp should first be set to num1, not num2. c. The swap function must use reference parameters. d. The last line should be temp = num1. e. Nothing is wrong with this function.
The relation shown in Figure 15.11 lists members of staff (staffName) working in a given ward (wardName) and patients (patientName) allocated to a given ward. There is no relationship between members of staff and patients in each ward. In this example assume that staff name (staffName) uniquely identifies each member of staff and that the patient name (patientName) uniquely identifies each patient.
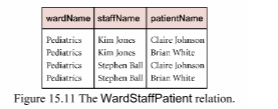
(a) Describe why the relation shown in Figure 15.11 is in BCNF and not in 4NF.
(b) The relation shown in Figure 15.11 is susceptible to update anomalies. Provide
examples of insertion, deletion, and update anomalies.
(c) Describe and illustrate the process of normalizing the relation shown in Figure 15.11 to 4NF.
A user should be able to complete all related tasks under a single navigation form rather than having to move from form to form to find different tasks
Indicate whether the statement is true or false
A report that is embedded within another report
a. Bound report b. Subreport c. Subform