Perhaps the most common form of protection from unauthorized use of a computer system is the ____.?
A. ?password
B. ?certificate
C. ?PKI
D. ?digital signature
Answer: A
You might also like to view...
Match the following terms to their meanings:
I. Import II. Append III. Export IV. Convert V. Merge A. Send out a copy of data from application to another B. Change to a different format or type C. Bring in a copy of data from application to another D. Combine a main document and a data source to create a letter or memo E. Add data from another table to the end of the existing table
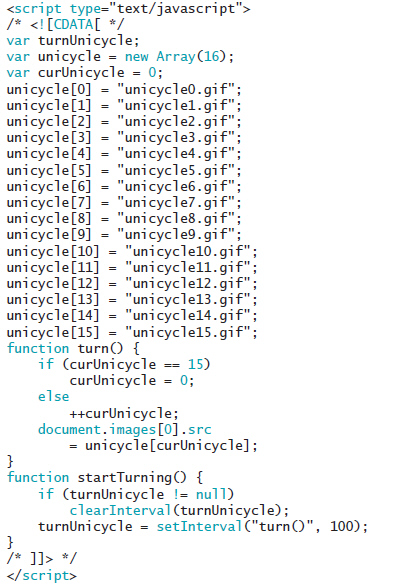 The script seen in the accompanying figure ____.
The script seen in the accompanying figure ____.
A. creates an animation B. will cause an error C. will execute the turn() function every 100 seconds D. contains an array named curUnicycle
Desktop motherboard DIMM slots have _______ that keep the module firmly connected in the memory slot
Fill in the blank(s) with correct word
A function ____ is simply an object or data element that is accessed by an assigned name within the function.
A. parameter B. code C. behavior D. sequence