Describe the differences between eavesdropping and skimming.
What will be an ideal response?
Eavesdropping is surreptitiously obtaining data from an unknowing end user who is performing a legitimate function. An example involves having a hidden sensor
co-located with the legitimate sensor. Skimming is the act of obtaining data from an unknowing end user who is not willingly submitting the sample at that time. An example could be secretly reading data while in close proximity to a user on a train.
You might also like to view...
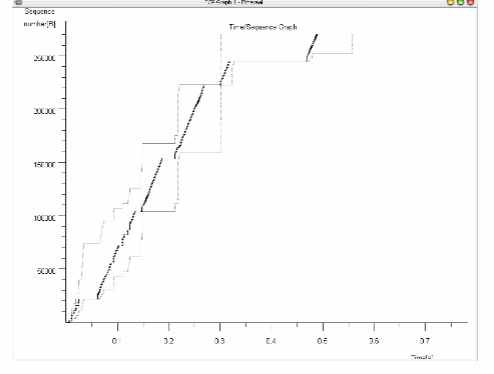
Try to observe periods when the TCP sender is in a slow start phase and when the sender switches to congestion avoidance. Verify that the congestion window flows the rules of the slow start phase.
Decorative formats such as outlines, shadows, text glow, and colors are called ________
A) themes B) font styles C) illustrations D) text effects
Critical Thinking QuestionsCase 2Your friend Rita comes to you for help organizing her files, all of which are currently stored on a USB flash drive. You suggest that she create a folder for each class that she is taking. In addition, you suggest that she create folders within each class folder, one for each topic that the class covers. Rita takes your suggestion and creates a folder called Hist201 for her American history class. Inside the Hist201 folder, she creates folders called CivilWar and Slavery. Rita saved a document to one of the folders she created, but now she cannot recall which one. What should she use to locate the document? a.the search boxc.the ribbonb.the Refresh buttond.the address bar
What will be an ideal response?
______ electronic commerce applications support transactions between governments such as the federal government and state or local governments.
Fill in the blank(s) with the appropriate word(s).