In a ________ network users log in to the network instead of their local computers and are granted access to resources based on that login
A) peer-to-peer B) server C) local area D) client-server
D
Computer Science & Information Technology
You might also like to view...
Determine the router hop count from LAN A to LAN D in the network shown in Figure 8-12 for the route with the fewest hops.
Figure 8-12
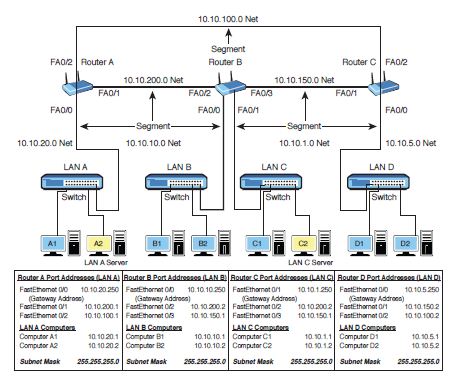
Computer Science & Information Technology
Which of the following involves the study and understanding of the operational details of the other company in a merger?
A. due care period B. due diligence period C. gap analysis D. dephi technique
Computer Science & Information Technology
Connector tools connect shapes with a(n) ____________________ or arrow.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
What should you use when you want to use one object to cut a hole in to another object?
A. Compound object B. Compound path C. Compound vector graphic D. Compound points
Computer Science & Information Technology