FIGURE AC 6-1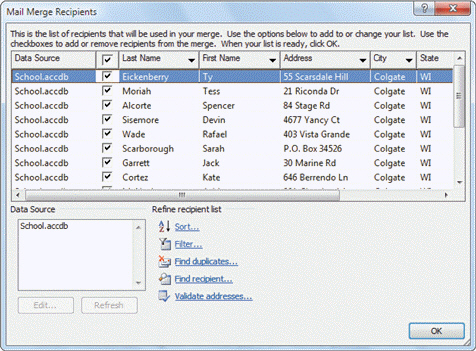 Referring to Figure AC 6-1 above, the following is NOT a field in the data source: ____.
Referring to Figure AC 6-1 above, the following is NOT a field in the data source: ____.
A. Address
B. City
C. Data Source
D. Last Name
Answer: C
Computer Science & Information Technology
You might also like to view...
This is a security mechanism that can be implemented on a network to register, authenticate, authorize, and enforce.
What will be an ideal response?
Computer Science & Information Technology
The term "internal connections" refers to all connections outside the network's control.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
In spreadsheet software, each cell has a unique cell ____.?
A. ?form B. ?address C. ?macro D. ?vector
Computer Science & Information Technology
_______________ or email are the two main ways that you can deliver an interactive form to your intended users.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology