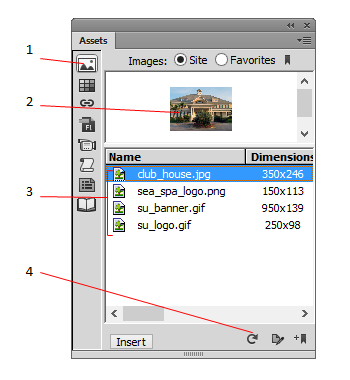
In the figure above, which number points to the thumbnail?
A. 1
B. 2
C. 3
D. 4
Answer: B
Computer Science & Information Technology
You might also like to view...
Which wireless security protocol is considered to be too weak for use inmost network settings?
A. WAP B. WPA C. WPA2 D. WEP
Computer Science & Information Technology
What are the two parts of cloning?
A. capture, sample B. sample, clone C. capture, clone D. clone, paste
Computer Science & Information Technology
The ribbon has exactly the same tabs, buttons, and features in every Microsoft Office program
Indicate whether the statement is true or false
Computer Science & Information Technology
____ are the levels within an InDesign document on which objects appear.
A. Levels B. Layers C. Libraries D. Merges
Computer Science & Information Technology