A user's remote marketing server has changed IP address schemes and now the user can no longer access it. The user further discovers that the distant end still has access to them. Which of the following is a possible cause?
a) SNMP strings need to be added
b) Firewall rules need to be configured
c) Port bonding on the interface needs to be enabled
d) The switch has lost power
Answer: b) Firewall rules need to be configured
You might also like to view...
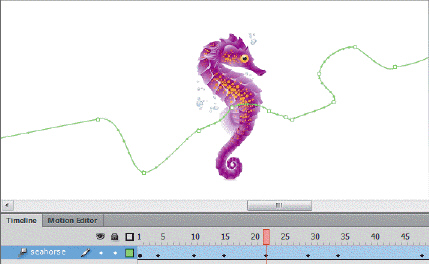 In the accompanying figure, as indicated in the Timeline, property keyframes only appear in motion tweens.
In the accompanying figure, as indicated in the Timeline, property keyframes only appear in motion tweens.
Answer the following statement true (T) or false (F)
Critical Thinking QuestionsCase E-1Stephan, an amateur photographer, is new to the game of analyzing the appearance of images and using Photoshop to improve the quality of his images. He has been surfing around the web looking for pointers, and has come across several new terms to add to his photography vocabulary. Stephan also learned that when he can see all of the transitions from dark to light in a grayscale image, it is called ____.
A. continuous tone B. smooth transition C. stair-stepping D. blocked transition
Microsoft's cloud storage is called ________ .
Fill in the blank(s) with the appropriate word(s).
Sara, the Chief Information Officer (CIO), has requested an audit take place to determine what services and operating systems are running on the corporate network. Which of the following should be used to complete this task?
A. Fingerprinting and password crackers B. Fuzzing and a port scan C. Vulnerability scan and fuzzing D. Port scan and fingerprinting