?A(n) _______ is an individual who captures trade secrets and attempts to gain an unfair competitive advantage.
Fill in the blank(s) with the appropriate word(s).
industrial spy
You might also like to view...
The transactions T, U and V use strict two-phase locking and their requests are interleaved as follows:
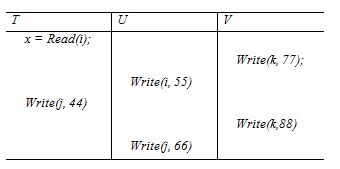
Assuming that the recovery manager appends the data entry corresponding to each Write operation to the log file immediately instead of waiting until the end of the transaction, describe the information written to the log file on behalf of the transactions T, U and V. Does early writing affect the correctness of the recovery procedure? What are the advantages and disadvantages of early writing?
Which of the following escape sequences represents a carriage return?
a. \n. b. \r. c. \cr. d. \c.
Emptying the Recycle Bin frees up space on the hard drive
Indicate whether the statement is true or false
In fold boundary the left and right numbers are folded on a fixed boundary between them and the ____ number.
A. first B. last C. center D. median