The opposite of asymmetric encryption is ____ encryption, in which one key is used to encrypt and decrypt.?
A. ?available key
B. ?asymmetric key
C. ?symmetric
D. ?public key
Answer: C
Computer Science & Information Technology
You might also like to view...
Give the method header the following method:
Method Smallest, which takes three integers x, y and z and returns an integer.
Computer Science & Information Technology
An SQL statement is an instruction using ________
A) Standard Question Language B) Standard Query Language C) Structured Query Language D) Structured Question Language
Computer Science & Information Technology
Flash Fillenters text based on _____.
A. ?the order of numbers assigned to the text in each cell B. ?the concatenate formula C. ?patterns it finds in the data D. ?conditional formatting assigned by the user
Computer Science & Information Technology
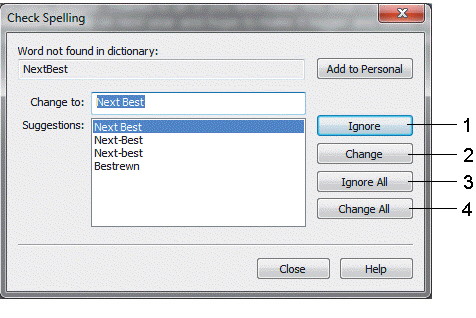 Click the item marked ____ in the accompanying figure to ignore all instances of a word.
Click the item marked ____ in the accompanying figure to ignore all instances of a word.
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology