In public-key encryption, the two keys, one for coding and one for decoding, are known as ________.
A. code keys
B. linked keys
C. key tags
D. a key pair
Answer: D
Computer Science & Information Technology
You might also like to view...
_________ combines the formatting strengths of HTML 4.0 and the data structure and extensibility strengths of XML.
a. HML b. SGML c. HTML5 d. XHTML
Computer Science & Information Technology
In the accompanying figure, box _____ points to the command to change to a new drive.
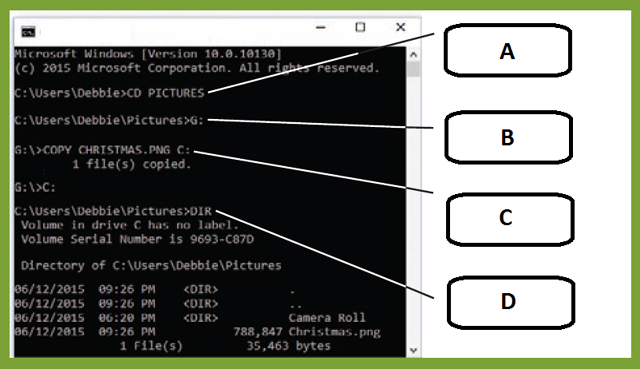
A. ?A B. ?B C. ?C D. ?D
Computer Science & Information Technology
As you continue to click the ________ button in the Evaluate Formula dialog box, each part of the formula is calculated until you reach the final result
Fill in the blank(s) with correct word
Computer Science & Information Technology
To add options to a selection list, it is best to follow the ECMAScript recommendations of using the add() method of the Select object to add new options to a selection list.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology