The __________ destructor is called before the __________ destructor.
a. base, derived
b. derived, base
c. public, private
d. private, public
e. None of these
b. derived, base
Computer Science & Information Technology
You might also like to view...
If the date formats available in Excel are not suitable, you can create a(n) ________ date format
Fill in the blank(s) with correct word
Computer Science & Information Technology
What are the two of the most important aspects of Linux?
What will be an ideal response?
Computer Science & Information Technology
Most authoring packages include visual effects such as:
a. panning, zooming, and tilting. b. wipes, fades, zooms, and dissolves. c. morphing. d. tweening. e. inverse kinematics.
Computer Science & Information Technology
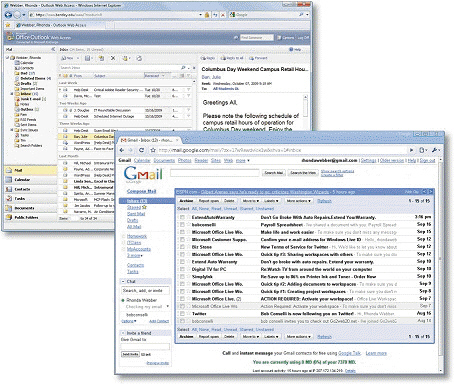 Both Gmail and ____ Web Access provide access to e-mail messages from within the browser, as shown in the accompanying figure.
Both Gmail and ____ Web Access provide access to e-mail messages from within the browser, as shown in the accompanying figure.
A. Microsoft Hotmail B. Mozilla Firefox C. Windows Internet Explorer D. Microsoft Office Outlook
Computer Science & Information Technology