Describe the meet-in-the-middle attack.
What will be an ideal response?
The meet-in-the-middle attack is an attack that makes use of a space-time trade-off. If you are willing to use more CPU time, you can reduce the memory requirement. For breaking 2DES, the time-memory product remains at 2112. The attacker attempts to find a value in each range and domain of the composition of two functions such that the forward mapping of one through the first function is the same as the inverse image of the other through the second function. In other words, the meet-in-the-middle attack quite literally attacks by finding the meeting point in the middle of the composed function.
You might also like to view...
What happened to the web browser window when the process was killed?
Step 1. Download Windows SysInternals Suite.
a. Navigate to the following link to download Windows SysInternals Suite:
https://technet.microsoft.com/en-us/sysinternals/bb842062.aspx
b. After the download is completed, extract the files from the folder.
c. Leave the web browser open for the following steps.
Step 2. Explore an active process.
a. Navigate to the SysinternalsSuite folder with all the extracted files.
b. Open procexp.exe. Accept the Process Explorer License Agreement when prompted.
c. The Process Explorer displays a list of currently active processes.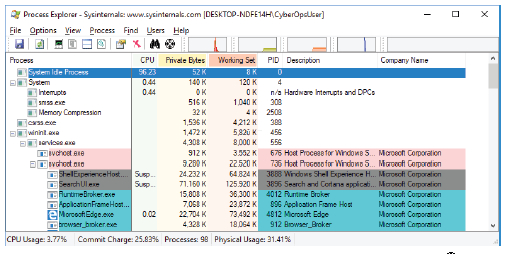
d. To locate the web browser process, drag the Find Window’s Process icon ( ) into the
) into the
opened web browser window. Microsoft Edge was used in this example.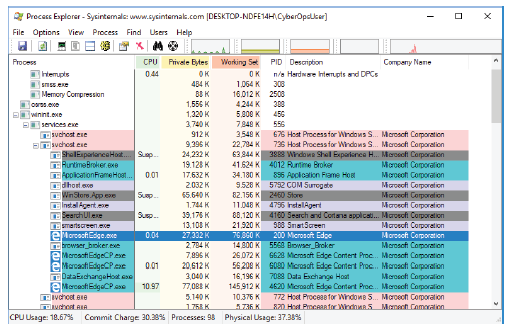
The primary difference between the ordered and unordered associative containers is ____________.
Fill in the blank(s) with the appropriate word(s).
Which of the following is not a possible value of
- attribute TYPE?
(a) 1 (b) A (c) I (d) R
With ____ editing, Word automatically displays a Paste Options button near the pasted or moved text.
A. drag-and-drop B. inline C. copy-and-carry D. cut-and-paste