Try doing chromakey in a range—grab something out of its back- ground where the something is only in one part of a picture. For example, put a halo around someone’s head, but don’t mess with the rest of their body.
What will be an ideal response?
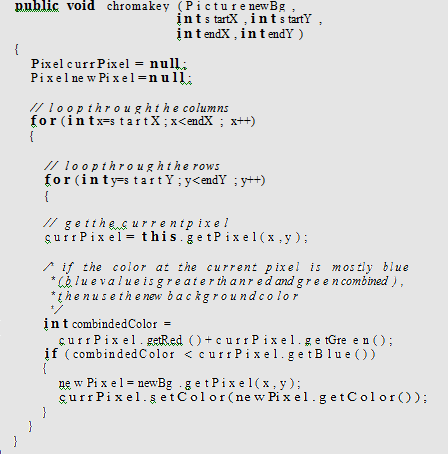
You might also like to view...
Answer the following statements true (T) or false (F)
1) Polymorphism helps promote software extensibility. 2) If a derived class reference is assigned to a base class variable, the variable must be cast back to the derived class before any derived class methods can be called with it. 3) The abstract methods and properties of a class do not provide an implementation. 4) Concrete classes provide implementations for every method and property they define.
To manage the security information from the devices in a large network, you should establish a security incident _________________ team.
Fill in the blank(s) with the appropriate word(s).
A(n) ________ is a set of rules for communication between devices that determine how data is formatted, transmitted, received, and acknowledged
Fill in the blank(s) with correct word
Which is the router command used to copy the running-configuration to NVRAM?
A) copy run show B) copy run flash C) copy run tftp D) copy run start