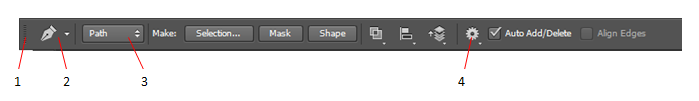
In the figure above, the number 2 refers to the _____ button.
Fill in the blank(s) with the appropriate word(s).
Pen tool
Computer Science & Information Technology
You might also like to view...
Which of the following is the only way to truly defend against session hacking?
A) Stateful packet inspection B) Encrypted transmissions C) IP spoofing D) Filtering routers
Computer Science & Information Technology
b) The process of instructing the computer to solve a problem is called _________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
What is the first thing that the kernel does when WinLoad turns over the startup process to it?
What will be an ideal response?
Computer Science & Information Technology
________ is the process used to bring in a copy of data from one sources or application to another application
A) Importing B) Transporting C) Merging D) Exporting
Computer Science & Information Technology