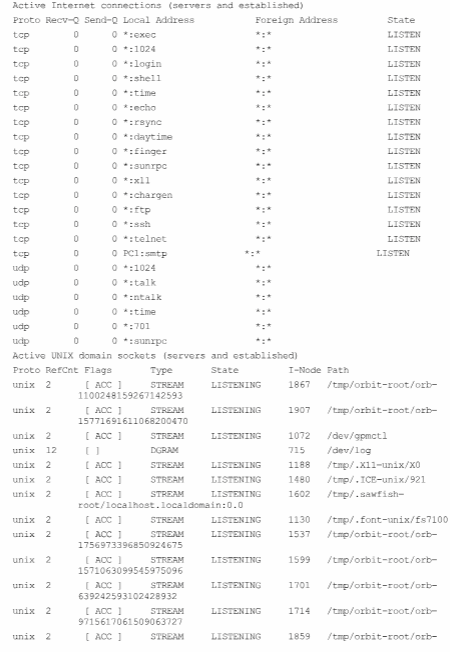
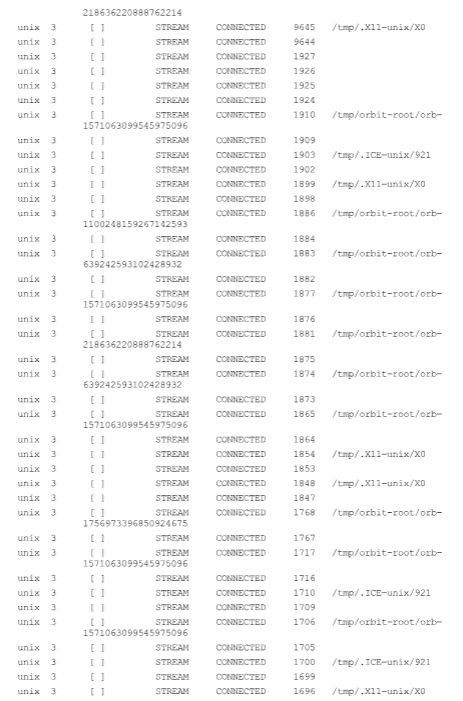
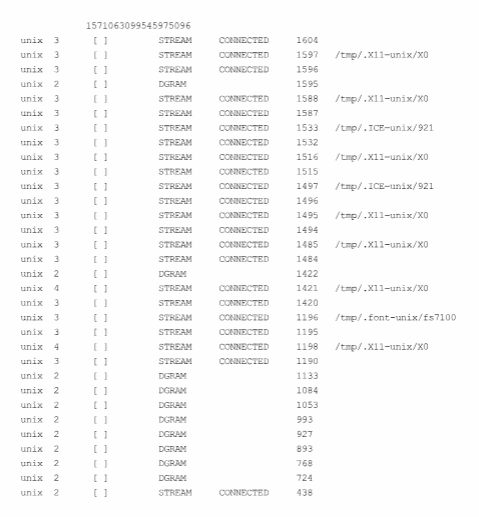
Attach the saved output to your report. Using the saved output, answer the following questions.
What will be an ideal response?
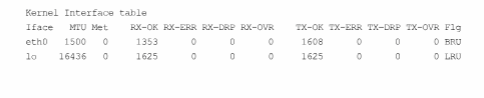
You might also like to view...
Which of the following choices is not one of the three security objectives that are considered when determining the impact of an information system?
A. Confidentiality B. Integrity C. Availability D. Authority
If a VBA error occurs while Access is running a procedure, you are offered the choice of ending the procedure or entering debugging mode. Choosing to end the procedure opens the Visual Basic Editor with the incorrect line of code highlighted in blue
Indicate whether the statement is true or false
Which of the following technologies uses software to emulate multiple hardware environments that can utilize multiple operating systems?
A. hypervisor B. containers C. thin provisioning D. virtualization
You can distort a type layer beyond the limits of stretching a bounding box by using the Warp Screening feature.
Answer the following statement true (T) or false (F)