What are the handles pointing to?
What will be an ideal response?
Step 1. Explore threads.
a. Open a command prompt.
b. In the Process Explorer window, right-click conhost.exe and Select Properties….. Click
the Threads tab to view the active threads for the conhost.exe process.
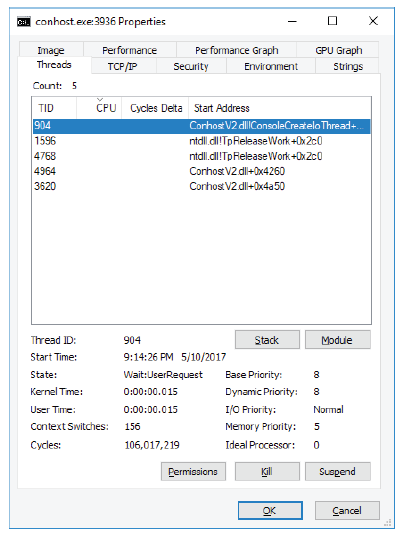
c. Examine the details of the thread.
Step 2. Explore handles.
In the Process Explorer, click View > select Show Lower Pane > Handles to view the handles
associated with the conhost.exe process.
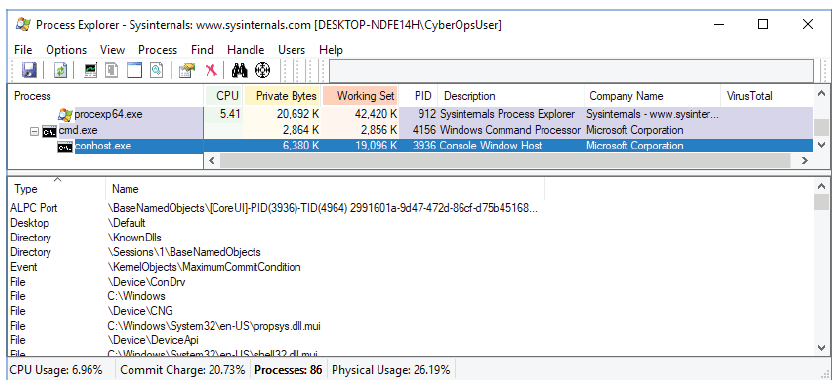
Examine the handles.
The handles are pointing to files, registry keys, and threads.
You might also like to view...
________ is the illegal use of email to scam users into surrendering their personal information, usually items like Social Security numbers, bank account numbers, and credit card numbers.
Fill in the blank(s) with the appropriate word(s).
Match the following functions to their actions:
I. Lines A. Used to highlight critical information on a report. II. Conditional Formatting B. Used to produce data on a report III. Calculated Fields C. Provides summaries of report groups. IV. Group and Report Totals D. Used to separate sections of a report
In most programming languages, global variables are declared explicitly as global or declared in the main module outside any other modules.
Answer the following statement true (T) or false (F)
The Secure Hash Algorithm (SHA) was developed by the _________ and published as a federal information processing standard (FIPS 180) in 1993.
Fill in the blank(s) with the appropriate word(s).