A ____ is one in which the computer system enforces the controls without the input or intervention of the system or data owner.
A. role based control
B. network access control (NAC)
C. mandatory access control (MAC)
D. discretionary access control (DAC)
Answer: C
You might also like to view...
Write a method called switchThem that accepts two integer arrays as parameters and switches the contents of the arrays. Take into account that the arrays may be of different sizes.
What will be an ideal response?
TOSLINK is associated with HDMI ports
Indicate whether the statement is true or false
To show the subnet for an address, IPv6 uses the "/X" _______________ nomenclature.
Fill in the blank(s) with the appropriate word(s).
The U.S. Immigration and Naturalization Service keeps records of where persons entering the United States and seeking to stay come from originally. The following graph shows where immigrants came from during the 1990s. 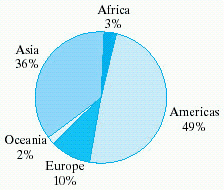 If there were approximately 7.7 million immigrants to the United States during the 1990s, about how many came from Asia?
If there were approximately 7.7 million immigrants to the United States during the 1990s, about how many came from Asia?
A. 277.2 immigrants B. 2.772 immigrants C. 27,720,000 immigrants D. 2,772,000 immigrants E. 2,772 immigrants