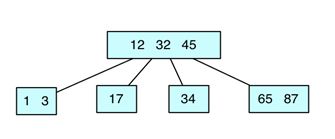
Draw the 2-4 tree that results from adding the following elements into an initially empty tree:
34 45 3 87 65 32 1 12 17
You might also like to view...
The Users tab enables you to see who is logged in to a computer
Indicate whether the statement is true or false
Case-Based Critical Thinking Questions ?Case 5-2 In PowerPoint 2016, Laura is putting together a year-end presentation of the highlights of her Cheerleading Squad competitions. She wants to insert slides from a prior presentation. ? Laura wants the slides from the previous presentation to appear after Slide 4. On the Home tab, in the Slides group, she clicks the ____ button arrow and then clicks Reuse Slides.
A. Reuse Slide B. New Slide C. Edit Slide D. Insert Slide
Before secure methods were created for making remote connections over the Internet, the biggest drawback to private remote connections was the cost to connect.
Answer the following statement true (T) or false (F)
Pete, a network administrator, is capturing packets on the network and notices that a large amount of the traffic on the LAN is SIP and RTP protocols. Which of the following should he do to segment that traffic from the other traffic?
A. Connect the WAP to a different switch B. Create a voice VLAN C. Create a DMZ D. Set the switch ports to 802.1q mode