Consider the following heap:78 67 32 56 8 23 19 45What would be the heap obtained after calling deleteHeap?
A. 67 56 32 45 8 23 19
B. 67 32 56 8 23 19 45
C. 78 32 56 8 23 19 45
D. 78 67 32 56 8 23 19
Answer: A
You might also like to view...
Create a rough sketch of your game in both 4:3 and 16:9 formats. Will one of the formats in particular enhance the way your game is played?
What will be an ideal response?
The methodology used by web project teams is usually:
a. the SDLC b. a derivative of the SDLC similar to the one discussed in this chapter c. decided on as the project is built d. web sites do not require the use of a development methodology
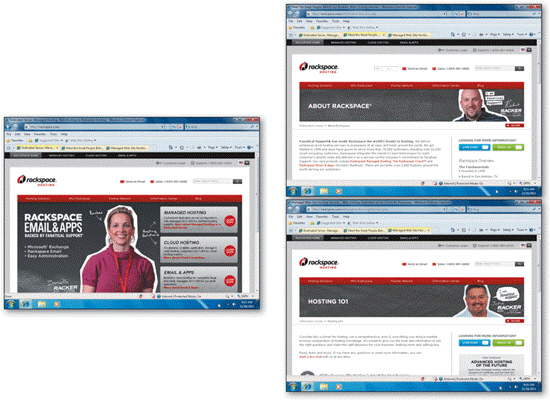 The consistent application of _________________________ and repeating content elements across all the pages at a site unifies its look and feel, as shown in the accompanying figure.
The consistent application of _________________________ and repeating content elements across all the pages at a site unifies its look and feel, as shown in the accompanying figure.
Fill in the blank(s) with the appropriate word(s).
A vulnerable process that is divided between two or more individuals to prevent fraudulent application of the process is known as which of the following?
A. separation of duties B. process sharing C. mandatory splitting D. role reversal