Which of the following malware types typically allows Pete, an attacker, to monitor a user's computer, is characterized by a drive-by download, and requires no user interaction?
A. Virus
B. Logic bomb
C. Spyware
D. Adware
Answer: C. Spyware
You might also like to view...
Most commercial _________________ include(s) an online catalog, a shopping cart, and a secure order form.
a. web host providers b. shopping cart software c. web server software d. e-commerce hosting packages
Define the Fresnel zone.
What will be an ideal response?
The __________ contains a summary of changes in a document.
Fill in the blank(s) with the appropriate word(s).
The state diagram below represents one of the many possible 2?bit state machines that can be used to perform prediction. Explain, in plain English, what it does.
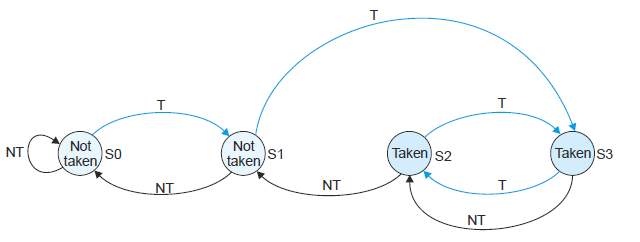
1. If you are in state S1 (not taken) and the next branch is taken, you go straight to state S3, the strongly taken
state.
2. If you are in state S3, a taken branch takes you to state S2 (rather than back to state S3). State S3 is not a
saturating state. If there is a sequence of taken branches, the system oscillates between S2 and S3. From
state S3 the next state is always state S2 (since a taken and a not taken have the same destination).