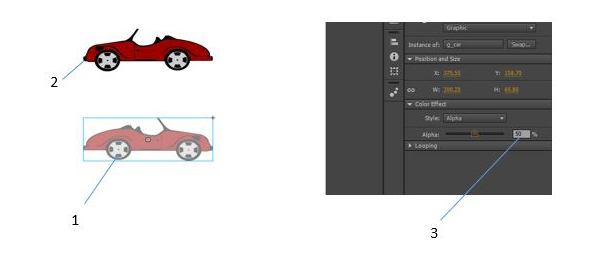
 ?
?
In the figure above, there are two different symbols on the stage.
Answer the following statement true (T) or false (F)
False
You might also like to view...
A successful hijacking takes place when a hacker intervenes in a TCP conversation and then takes the role of either host or recipient.?
Answer the following statement true (T) or false (F)
The loop can best be categorized as a __________.
``` z = 0; g = 0; s = 0; i = 0; while (i < 50) { scanf("%d", &t); s = s + t; if (t >= 0) g = g + 1; else z = z + 1; i = i + 1; } ``` a. counter-controlled loop b. sentinel-controlled loop c. loop that computes a product d. general conditional loop e. none of the above
What are the necessary ingredients of a greedy algorithm?
a. Optimal substructure and greedy choice b. Recursion and greedy choice c. Priority queue and optimal substructure d. Recombination and greedy choice
A(n) ________ IF function increases the logical outcomes that can be expressed
Fill in the blank(s) with correct word