The individuals responsible for generating images for websites are referred to as
a. network administrators.
b. graphic designers.
c. web programmers.
d. interface designers.
B
You might also like to view...
Effective incident reporting relies on the presence of a well-established ____ function.
A. recording B. controlling C. monitoring D. responding
Design a deterministic network evolution model for the following scenario: At time t = 0, a node, called as root hub node, is present in the network. At t = 1, N ? 1 nodes leaf nodes are introduced. At t = 2, two units of the subnetwork, formed during t = 1, are introduced, and then links are added between the leaf nodes and the root hub node. The above process continues until t = n. Estimate the scaling exponent for this network model as a function of N.
What will be an ideal response?
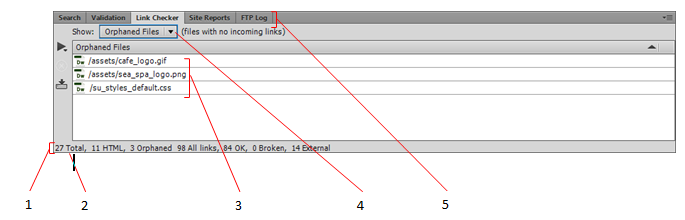
Answer the following statement true (T) or false (F)
_________ audit trails are generally used to monitor and optimize system performance.
A. User-level B. Physical-level C. System-level D. All of the above