Draw a task model of the system design of the MyTrip system presented in Chapter 6, System Design: Decomposing the System.
What will be an ideal response?
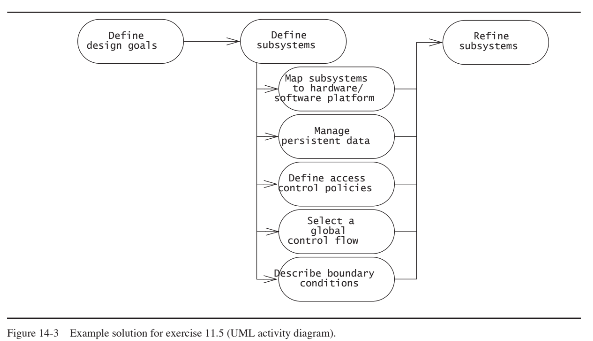
A task plan can be represented as an activity diagram. The MyTrip system was used as an example to illustrate each
system design activity. Hence, the activity diagram of Figure 6-28 can be used as a starting point for the solution to
this exercise. We remove the “Implement Subsystem” activity (it is not part of system design) and add a “Refine
subsystems” activity to plan for a second iteration (see Figure 14-2). A conservative manager may even want to
serialize all tasks instead of conducting the activities of system design in parallel.
You might also like to view...
Which of the following statements is false?
a) The HasValue property returns true if a nullable-type variable contains a value; otherwise, it returns false. b) The Value property returns the nullable-type variable’s underlying value. c) The null coalescing operator (??) has two operands. If the left operand is not null, the entire ?? expression evaluates to the left operand’s value; otherwise, it evaluates to the right operand’s value. d) All of the above statements are true.
A(n) ____________________ is a combination of letters, numbers, and symbols that verifies your identity.
Fill in the blank(s) with the appropriate word(s).
If a workbook contains grouped worksheets, this word will display on the title bar
A) [Collection] B) [Group] C) [Set]
Mary, a remote user, connects her Windows 10 laptop to the corporate network by way of the Internet using a VPN tunnel. Which of the following is often configured as a required step for a user each time she attempts to use the VPN connection?
A. Call the help desk at the corporate office to obtain a random VPN password. B. Configure the laptop to a static IP address on the corporate LAN subnet. C. Enter the same user name and password used on the corporate network. D. Select the encryption and authentication methods in Connection Properties.