________ contributes to a larger overhead in SRT than SPF
a) Accounting for potential user abuse
b) Estimating future process behavior
c) Performing preemptions
d) both a and b
c) Performing preemptions
You might also like to view...
Introduce specialization/generalization concepts into the ER model shown in Figure 13.11 and described in Exercise 12.13 to show the following:
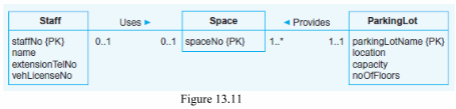
(a) The majority of parking spaces are under cover and each can be allocated for use by a
member of staff for a monthly rate.
(b) Parking spaces that are not under cover are free to use and each can be allocated for use
by a member of staff.
(c) Up to twenty covered parking spaces are available for use by visitors to the company.
However, only members of staff are able to book out a space for the day of the visit. There is no charge for this type of booking, but the member of staff must provide the visitor’s vehicle
license number.
A file that no longer works properly because it has been accidentally altered by hardware or software failure is said to be ________
Fill in the blank(s) with correct word
What does the HKEY_LOCAL_MACHINE root key contain?
What will be an ideal response?
What is the default Pass Count with Windows Memory Diagnostic Tool?
A. 1 B. 2 C. 3 D. 4