____________________ are undesirable events associated with attacks or violations of information.
Fill in the blank(s) with the appropriate word(s).
Incidents
You might also like to view...
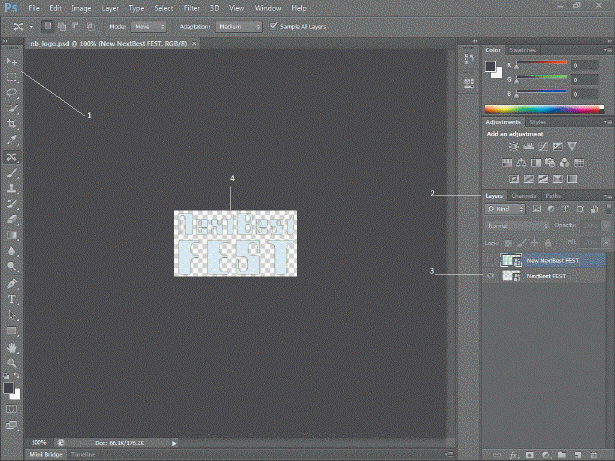 The item marked 2 in the accompanying figure is the ____ panel.
The item marked 2 in the accompanying figure is the ____ panel.
A. Layers B. Tools C. Visibility D. Property inspector
An algorithm may be too ____ to be of any use.
A. difficult to read B. inefficient C. difficult to create D. offensive
What does the ping message "Destination host unreachable" message mean?
A. The pinged host is on another network. B. The pinged host responded, but has an incorrect gateway configured. C. The pinged host's network is down. D. An ARP reply was not received.
Case-Based Critical Thinking Questions ? Case 1-1 Lucy wants to develop a web page to display her profile. She wants to just start with a basic page that lists her accomplishments, her work history, and the different computer courses she has taken. She would like each section to be clearly identified. ? Which type of list would work best for listing Lucy's accomplishments?
A. ?legends list B. ?header list C. ?definition list D. ?unordered list