Values and labels can be entered automatically using the fill handle and a technique called _____.
A. fill-and-drag
B. drag-and-fill
C. drag-and-drop
D. drag-and-paste
Answer: B
You might also like to view...
When should base class members be declared protected?
a. When all clients should be able to access these members. b. When these members are used only by member functions of this base class. c. When these members should be available only to derived classes (and friends), but not to other clients. d. The protected access specified should never be used.
Finish the C R C cards in Problem 1 by creating Object Think statements and property names for each of the five classes.
What will be an ideal response?
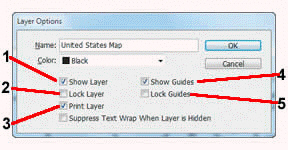 Which item in the accompanying figure shows that the layer will not be hidden?
Which item in the accompanying figure shows that the layer will not be hidden?
A. 1 B. 2 C. 3 D. 4
What is the term used to specify the fully qualified domain name assigned to a cluster, and must have an entry in DNS that resolves to the cluster's primary IP address?
A. Primary address B. Full Internet name C. Cluster address D. DNS name